|
|
In response to the evolving threat landscape, organizations are moving from their legacy layered network defense to a Zero Trust security model. 85% of organizations have already defined Zero Trust initiatives but often don’t know where to start. With Zero Trust, organizations follow the “never trust, always verify” approach, which dictates that endpoints, user identities, applications, and the corporate network are no longer trusted by default. SentinelOne is committed to helping organizations succeed as they shift to a Zero Trust security model.
With the rise of credential stuffing attacks and ransomware, endpoints and identities are two of the most commonly exploited attack vectors to gain access to an organization’s data.

Attacks like these have made organizations reconsider the ‘trust by default’ approach. Insider credentials are attractive targets for attackers as they can be taken advantage of for elevated access. In contrast to attacks originating from outside of the corporate network, adversaries can leverage the implicit trust given to an identity or endpoint to move laterally within an organization’s network.
Many customers today interconnect their endpoint and identity security solutions to gain complete visibility on compromised users. This is often done through their Security Information and Event Management (SIEM) or User and Entity Behavior Analytics (UEBA) solution.
However, this results in several disadvantages:
- Struggles with scalability
- Requires setup and maintenance of integration
- Limited automation opportunities for automatic remediation
- Lack of real-time detection and response, relying on logs and events after-the-fact to reconstruct attacks
- Lack of prevention capabilities to stop attacks from progressing, no automated response and recovery
As organizations move to a Zero Trust model, they are looking to understand how they can continuously verify the trust of all their assets and provide explicit just-in-time access. To achieve that, organizations are looking into Extended Detection and Response (XDR) as their modern security platform that can solve the data ingestion, data analytics and processing, and central response problem.
Adopting Zero Trust Model
Whereas legacy models focused on neutralizing threats originating outside an organization’s network, Zero Trust acknowledges that threats may well exist both inside and outside the network. Legacy security models trust by default the endpoints and identities within their sphere of influence; in contrast, Zero Trust follows the principle of “never trust, always verify” for all endpoints and identities.
By successfully adopting Zero Trust, organizations can perform risk-based access control and leverage the concept of least privileged access for every access decision. Organizations that successfully adopt a Zero Trust concept become more effective in protecting their assets and faster at responding to cyber threats. Ultimately, adopting Zero Trust will help organizations to reduce risk as well as Mean-time-to-Detect (MTTD) and Mean-time-to-Respond (MTTR).
SentinelOne for Zero Trust
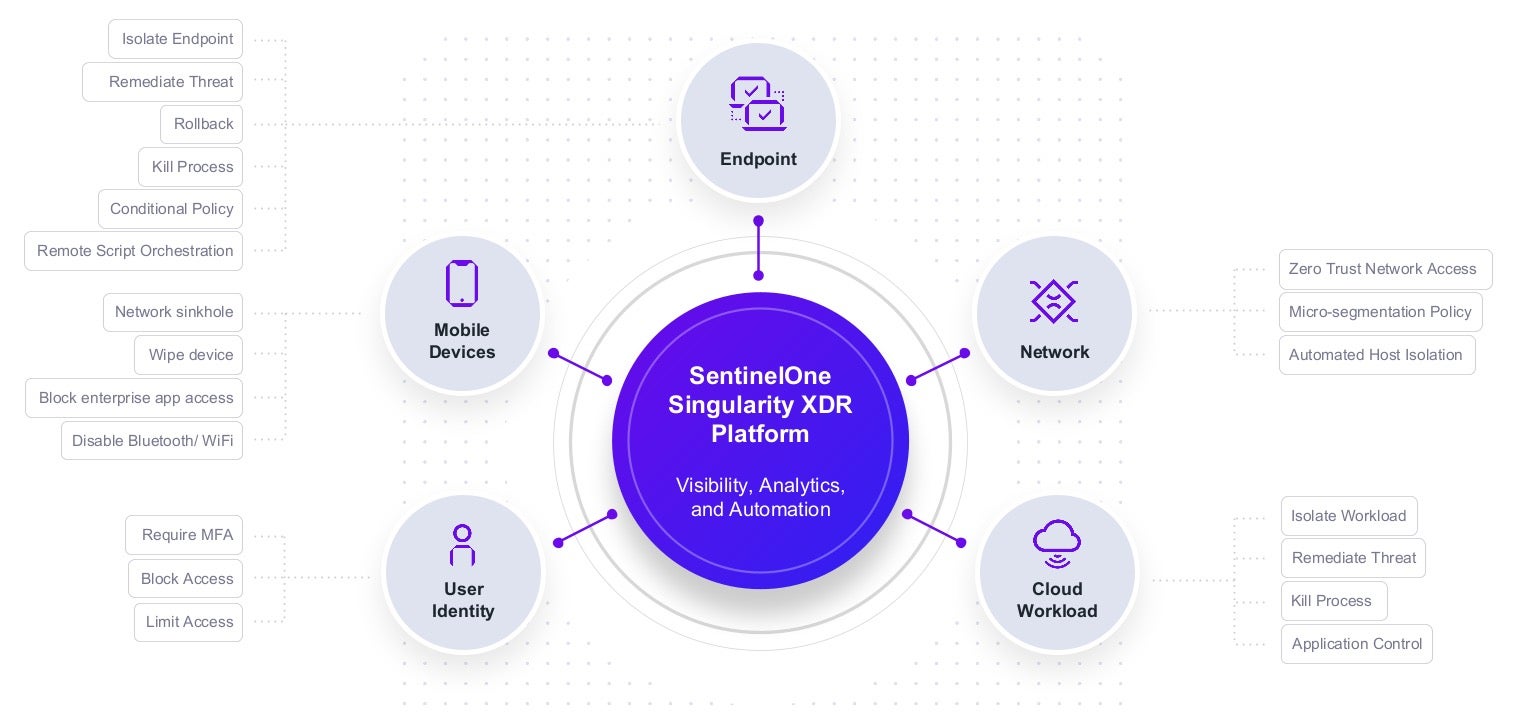
The SentinelOne Singularity XDR extends visibility, analytics, and response capabilities across endpoint, user identity, cloud applications, and the network, enabling Singularity XDR to power the organization’s Zero Trust security model.
To achieve that, SentinelOne has partnered with leading solutions in Identity and Access Management (IAM), Cloud Application Security Broker (CASB), and Network Detection Response (NDR) to provide a best-of-breed Zero Trust security model where organizations can choose the vendors of their own choice.
Protecting User Identity with Azure AD Integration
SentinelOne is a member of the Microsoft Intelligent Security Association and is excited to announce the general availability of the SentinelOne App for Azure Active Directory. The SentinelOne Singularity XDR Platform integrates Microsoft Azure Active Directory (Azure AD), a leading enterprise identity and access management solution, to provide Zero Trust capabilities for endpoints and identities. Through the integration, organizations benefit from autonomous response capabilities that help security professionals respond to cyber threats faster.
“Global cyberattacks attacks like Kaseya or SUNBURST are a constant reminder of the importance of modernizing legacy security architectures”, said Sue Bohn, Vice President of Program Management, Microsoft. “The integration between SentinelOne and Azure Active Directory will allow organizations to combine leading endpoint and identity solutions to embrace a Zero Trust security model.”
“Joint customers benefit from built-in integration for autonomous real-time response actions”, said Raj Rajamani, Chief Product Officer, SentinelOne. “Bringing together leading endpoint and identity solutions will go a long way towards helping customers develop and mature their Zero Trust programs”.
Through the SentinelOne App for Azure Active Directory, when an endpoint is compromised, the impacted user identity information is shared in real-time with Azure AD, allowing the organization’s Conditional Access policy to prevent access to corporate resources and services.
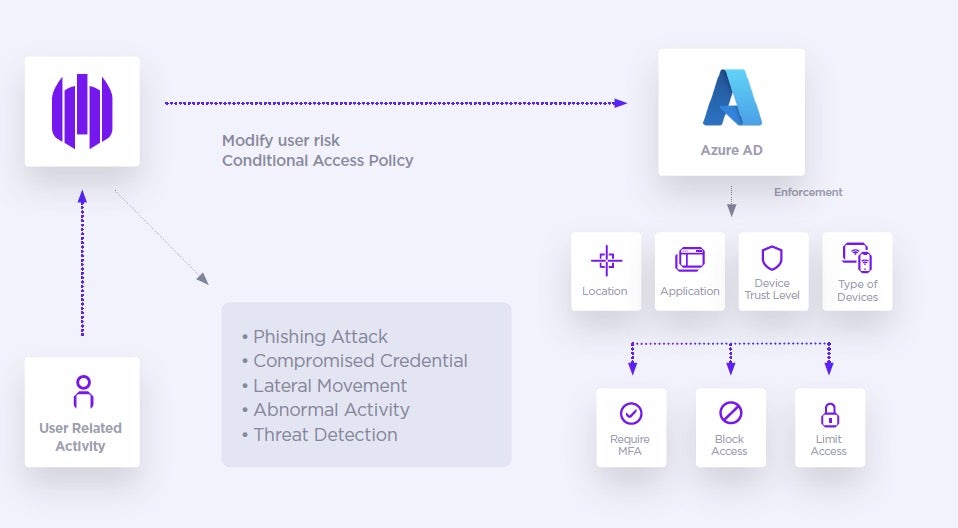
With SentinelOne and Microsoft, organizations can begin their Zero Trust journey by unifying endpoint security and identity management for conditional access. With seamless integration, connect SentinelOne Singularity XDR to Microsoft Azure AD to enforce identity policy and automatically respond to threats.
With this powerful integration, joint customers can:
- Enforce MFA for user identities authenticated on a compromised endpoint
When a user is authenticated on a compromised endpoint you can enforce MFA.
- Block access for compromised user identities
Block in real-time access to corporate resources and services for users authenticated on a compromised endpoint.
- Limit access for compromised user identities
Limit access to corporate information when the user is using a compromised endpoint.
- Hassle-free connection between Singularity and Azure Active Directory
No complex API work is required or manual maintenance required.
Monitor, Secure and Enforce Endpoint Policies
Today endpoints, regardless of whether they are workstations, laptops, mobile devices, or servers, often have different configurations, patch statuses, and operating systems, leading to inconsistent approaches to applying security policy. This problem is compounded by the rise of bring-your-own-endpoint (BYOD) and the loss of visibility from legacy network controls due to the rise of remote and hybrid working practices.
Adopting Zero Trust for endpoints can assist organizations in reducing this risk by providing the means to monitor, isolate, secure, control, and remove any endpoint from the network at any time. When integrated into a Zero Trust ecosystem, endpoints can provide valuable trust signals when determining whether to grant network access, including the endpoint’s identity, health, and compliance status.
SentinelOne Singularity XDR Protection combines next-gen prevention and Endpoint Detection Response (EDR) capabilities in a single platform with a single agent.
With Singularity, organizations benefit from:
- Robust Prevention & Control
Replace legacyAV solutions with Static AI models trained to detect threats by looking at various static attributes extracted from executables, eliminating dependencies on signatures, and offering superior detection of file-based threats.
- Threat Detection with Storyline™
Behavioral AI evaluates threats — like fileless attacks, lateral movement, and actively executing rootkits — in real-time, delivering high-fidelity detections without human intervention.Individual events are automatically correlated into a context-rich Storyline to reconstruct the attack from start to finish.
- Automated Remediation
Patented 1-click remediation automates threat resolution with fully autonomous responses that trigger protective actions in real-time. SentinelOne provides a clear picture of an endpoint’s health, management status, and the ability to automatically quarantine or remediate it to bring the device into compliance.
- Singularity Conditional Policy
Organizations struggle to balance between security and user productivity. When looking at security configurations, they typically treat all endpoints equally regardless if they are compromised. With Singularity Conditional Policy, organizations can change in real-time security enforcements depending on whether an endpoint is compromised.
- Device Hardening and Control
SentinelOne’s Device Control suite helps organizations embrace a more hardened posture for data loss prevention by restricting USB, Bluetooth, and Bluetooth Low Energy communications. Admins can restrict by endpoint class – for example, USB mass storage endpoints – which dramatically reduces the potential attack surface for insider threats and data loss.
Protect Cloud Workloads and Applications
According to Forrester, “public cloud migrations and other disruptive IT changes have often acted as a good vehicle for achieving a Zero Trust security model.”
A Zero Trust solution for cloud workloads must provide a repeatable and consistent approach to securing private, public, hybrid, and multi-cloud environments. Regardless of the public cloud environment, it’s the organization’s responsibility to monitor their cloud attack surface, which is just as vulnerable to compromise as user endpoints.
With Singularity Cloud Workload Security, organizations benefit from:
- Runtime Protection
Runtime protection and EDR for virtual machines (VMs) and containerized workloads. Organizations can manage and secure hybrid, private, and multi-cloud workloads from a single console with a single agent. Workload health status is available in real-time and affected workloads can automatically be brought back into compliance.
- Automated Application Control
Application Control preserves the immutable nature of the workload by employing a default-deny posture for any new code not present in the validated initial VM or container image. Not only does this harden the image itself, but it prevents attackers from executing arbitrary code that could be used for compromise or lateral movement.
- Cloud Application Access Control
Cloud application access control enables default-deny policies for access to cloud workloads and services. Cloud services are denied by default, reducing the amount of shadow IT and shadow cloud usage. Only approved endpoints will access the cloud resources and can be managed by exception by the security team.
Segment and Control Network Access
Networks have evolved due to the rise of remote work, and our perception of the network perimeter has evolved as well. Managed networks are no longer contained to a single location; they exist wherever devices, cloud workloads, and mobile devices access corporate resources.
With Singularity, organizations can better see and control their network with:
- Attack Surface Visibility and Control
To gain visibility into the network, SentinelOne Singularity Ranger turns endpoints into distributed network sensors that provide monitoring of the enterprise attack surface in real-time. SentinelOne agents actively fingerprint and inventory all IP-enabled endpoints on the network to identify abnormal communications and open vulnerabilities.With Ranger, risk from devices that are not secured with SentinelOne can be mitigated by either automatically deploying an agent or isolating the device from the secured endpoints. This is how Ranger can be used to effectively reduce the attack surface.
- Zero Trust Network Access
SentinelOne’s integrations with Zscaler and Cloudflare uses device signals from SentinelOne to inform ZTNA access decisions. Information about the endpoint, including whether it is managed and has a SentinelOne agent installed, is provided to Zscaler and Cloudflare. This information is combined with contextually relevant information from an identity provider to determine a point-in-time network access decision.
- Microsegmentation
SentinelOne’s integration with Guardicore provides centralized visibility of network activity, including network data generated from endpoints and cloud workloads. SentinelOne agents report metadata to Guardicore that creates detailed visibility and network topology in the Guardicore console for decision-making, forensics, and micro-segmentation policy creation. Policies can be exported from Guardicore, where SentinelOne’s native firewall controls enforce them. Guardicore can define segmentation and micro-segmentation policies and then use the SentinelOne APIs to enforce them on the agent.
- Network Detection Response
SentinelOne integrates with a number of NDR solutions including Vectra AI, Awake Security (Arista Networks), and Fidelis. The combination of SentinelOne’s EDR with partner NDR capabilities provides visibility, detection, and response for both managed and unmanaged endpoints. While NDR connects related network activity into a broader attack map, SentinelOne provides contextual awareness by enriching information coming from managed endpoints such as device name, last logged-in user, operating system details, and other endpoint characteristics. This provides comprehensive threat detection, rapid and effective response, endpoint containment, and forensic analysis capabilities.
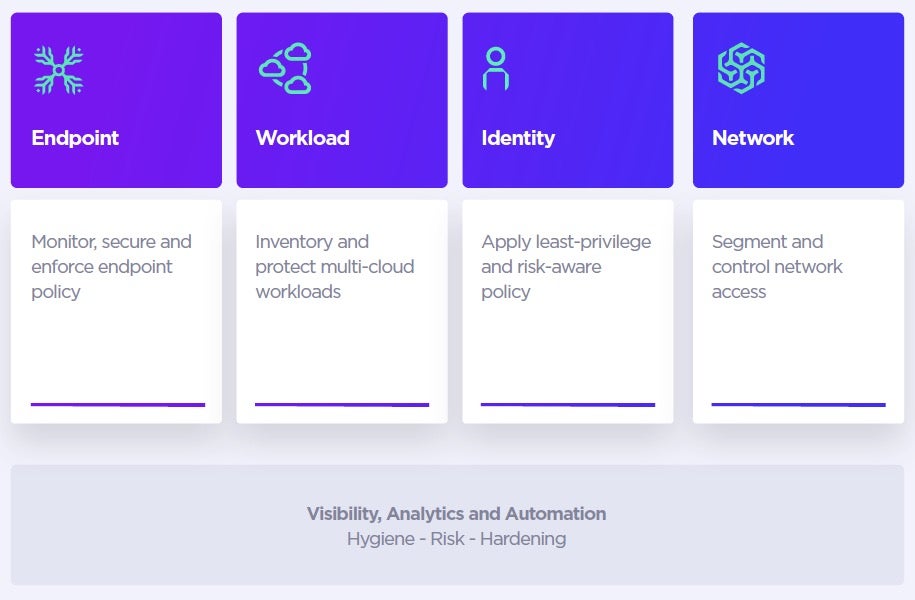
Summary
SentinelOne has partnered with other leading vendors to build the first-of-its-kind Zero Trust platform. Organizations have a wide variety of available vendors that can be integrated into a unified security platform, allowing organizations to benefit from data ingestion at scale, data analytics, and centralized autonomous response capabilities.
Want to learn more about SentinelOne for Zero Trust? Choose the path that suits you or your team best:
- Visit our Zero Trust webpage
- Download the white paper
- Register for the SentinelOne Zero Trust webinar



